Selecting the counter surveillance device that will help you ensure your privacy and safety
Whether you’re a high-level executive or business owner, or simply someone concerned about safety and privacy, you want to know whether you or your business are being watched or listened to against your will. If someone is spying on you, you have a right to know about it and put a stop to it. A broad range of counter surveillance tools is available on the market to help you identify potential spying devices and return to safety and privacy.
Commonly Used Bugging Devices
Sometimes people who deal with sensitive information are concerned that someone might be keeping tabs on their movements or listening in on their confidential conversations. Even in everyday life, people occasionally have concerns about being spied on, especially if they're involved in a lawsuit or some other controversial situation with another person where discretion is important. In your business, you may fear the competitors are listening in on confidential meetings, spying on product development, or tracking internal communications which discuss trade secrets.
There are a variety of ways that someone may secretly keep tabs on another person or business including:
- Monitoring the whereabouts of a vehicle using a GPS tracking device
- Placing an audio bug to listen in on private conversations
- Setting up a data bugging device to pull private files
- Hiding a covert camera to capture secret video
If you or your company are being watched in one of these ways, it is possible to use a detecting device to discover the bug. This is often accomplished using an RF (radio frequency) detector which identifies bugs transmitting an RF signal. When selecting your device, the first thing you will need to know is where various bugging devices fall on the RF spectrum to determine the most effective detector for your needs.
What is the RF Spectrum?
Radiofrequency, or RF, refers to the electromagnetic wave frequencies that lie in the range extending from around 3 kHz to 300 GHz. For our purposes, we’ll be referring to a much narrower range, somewhere between about 3 MHz and 6 GHz. These are the frequencies used for most communication transmissions.
Where Various Devices Fall on the RF Spectrum
Complete installed home security systems, DIY self-installed systems, and fully DIY systems each boast their benefits. Below is a comparison of the different features a user can expect from these three options:
| Frequency | Band Name | Abbreviation | Devices |
|---|---|---|---|
| 3-30 MHz | High Frequency | HF | Shortwave broadcasts, RFID |
| 30-300 MHz | Very High Frequency | VHF | FM radio, TV broadcasts, mobile communication |
| 300-3000 MHz | Ultra High Frequency | UHF | TV broadcasts, microwave appliances, mobile phones, wireless LAN, WiFi routers, Bluetooth, Zigbee, GPS, 4G, 2-way radios, cordless phones, baby monitors |
| 3-30 GHz | Super High Frequency | SHF | Wireless LAN, WiFi routers, cable and satellite TV broadcasting, GPS, 4G, cordless phones |
Audio bugging devices and hidden cameras may appear as cellular, Bluetooth, or WiFi signals, while certain other transmission signals will almost always fall within a specific range:
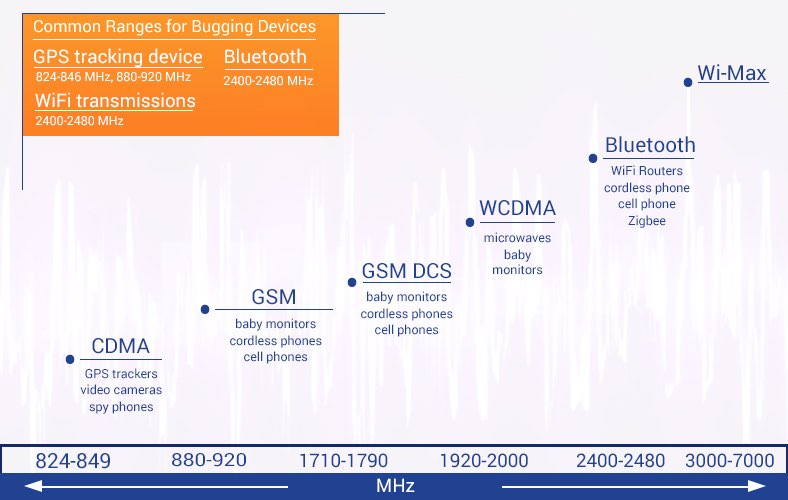
- Bluetooth transmissions: 2400-2480 MHz
- GPS tracking devices: 824-846 MHz, 880-920 MHz
- WiFi transmissions: 2400-2480 MHz
Various bugging devices may utilize different radio frequencies depending on how the devices are used. For example, an audio bugging device may appear as a cellular signal if it is set up through a cell phone, or if it is a device specifically for surveillance, it may utilize a Bluetooth or WiFi signal for transmitting audio and data back to another location. It is important to note that a hidden camera may use one of these signals if the information it captures is transmitted back to the source. However, if a hidden camera is not transmitting live, it may not project a signal and, a hidden camera lens finder will be a better option to uncover that device.
How Bug Detectors Work
When selecting the appropriate bug detecting device for your needs, it’s important to make sure that you know the RF signal produced by the particular kind of bug that you're looking for.
Depending on the bug detector model you are using, the process of scanning for a bug may vary slightly but should be similar across devices. Before you begin, you should turn off, unplug, and disconnect any communication devices you are already aware of in the space you’re scanning. Once done, turn on your RF detecting device. The way this works will be slightly different depending on the level of the detector you’re using. For example, a higher-end and more expensive detector may have a broad enough range to scan a large space all at once, while a lower- to the mid-range detector may only be able to scan for bugging devices up to about 20 feet away.
No matter which type of RF detector you're using, take your time with the scanning process and be patient. Some bugging devices may not register a signal immediately, so you may need to continue the scan while waiting for a transmission. For example, a GPS tracker placed in a vehicle could be programmed to transmit data back to the user who placed it every 10 seconds, or it could be programmed to only transmit every 10 minutes. It depends on how the user programmed the device. Because of this, it may be necessary to turn on the detector and wait until the bugging device you’re looking for makes a transmission. Until that time, a signal will be undetectable.
Once a signal registers, it’s important that you can recognize what the signal means. The common signal designations that you may see on an RF detecting device include:
- CDMA 824-849 MHz (GPS tracking devices, video cameras, spy phones)
- GSM 880-920 MHz (GPS tracking devices)
- GSM 880-920 MHz (GPS tracking devices)
- WCDMA, 3G, GSM (PCS), DECT 1920-2000
- Bluetooth, WiFi 2400-2480 (Audio and data bugging devices)
- Wi-Max 3000-7000
Counter Surveillance Detectors to Find Bugging Devices
The average counter surveillance detecting device will be able to identify most RF signals from typical bugging devices. Simple, low-cost detecting devices will enable you to identify if there are unexpected signals in your office or home, but these devices may have limitations as well. Higher-end and higher-cost detection devices may be more useful, depending on your specific needs. Below is a breakdown of some popular bug-sweeping devices on the market and how they can be used to ensure your privacy.
The Good, Better, and Best of Bug Detectors
Some of the most affordable RF signal detectors feature simple interfaces that light up to show which signals were detected in a space, while others may include strength meters to show how strong these signals are. These devices fall in the lowest price range, usually under $300. While they will help you identify the presence of RF signals, they do not provide more specific information about the signal so, a bit of leg work will be required. Once identified, you will need to examine the space carefully to find the source of the signal. These basic detecting devices are a good choice for homeowners, small business owners, and private citizens as they are not very expensive and can handle simple, on-the-go sweeps.
Median-range RF signal detectors come with a few more bells and whistles. Some portable bug detector kits come with signal blockers allowing you to block audio bugging devices while searching for them in your office or home. This added precaution is a great way to ensure privacy throughout the process of debugging. Some of these bug detectors also come with more detailed signal strength meters, allowing you to get a better picture of the signals you’re detecting as you move through your home or office in search of the bug. Mid-range devices like these are perfect for a business owner, lawyer, consultant, or other private services provider who needs to maintain privacy regularly. With a few extra features, these devices will cost a little more but are worth the investment.
The highest-end devices offered for bug detectors are for government agencies, law enforcement, and private investigators. Some of these advanced bug detectors feature signal blockers to prevent audio devices from working even before they have been found and deactivated. Signal blocking can also help users ignore signals they can identify such as authorized devices operating in an area while searching for the source of unidentified signals. The most costly detection devices on the market are most appropriate for professional settings where they will be reused or where detecting a bugging device is a matter of financial security. Often large corporations, law enforcement, private investigators, and high-level security teams will purchase these devices.
Other Counter Surveillance Detecting Devices
Some surveillance or bugging devices may not transmit signals at all, making them impossible to find with an RF signal detecting device. If your signal search has failed but you are still concerned about being bugged, there are other options for protecting yourself. Some hidden cameras, for example, may store video directly on the device or to an SD card, making transmissions unnecessary. Also, if you are using an RF signal detector and someone is spying on you via hidden camera, they could cut the feed when they see you searching, thereby eliminating the presence of a transmission signal. In these cases, using a hidden camera lens detector would be the better option as it helps you search for the presence of a camera without requiring you to search for a signal. Other counter surveillance options are signal blockers which can protect your privacy without requiring you to detect or disable surveillance devices.
If you’re concerned about someone infringing on your personal or professional security, there are counter surveillance devices available that can help you recover your peace of mind. Once you begin to understand how bugging devices and bug detecting devices work, you’ll be able to choose the best option to meet your needs.
Published February 15th, 2020
Updated September 24th, 2021
